Bitcoin itself is investment. Most people don’t understand this and spend them or try to invest them in scam sites.
today i will show you how to earn bitcoin and other coins without any investment so follow my steps
Some ways to earn bitcoins
Bitcoin is a cryptocurrency(virtual money) and a payment system invented by Satoshi Nakamoto in 2009. This is a is peer-to-peer system which means no one in involved between buyer and seller. You pay directly to other person any where in the world without need to have any bank account or transaction mode. Now you must be thinking how on earth we will verify these transactions. Well this is done by some unique network nodes(data communications equipment) which can create, send and receive information. All transactions are recorded in a public distributed ledger called the blockchain so that no one can scam you.
Create BitCoin Wallet for Free
First of all you need BitCoin Wallet in order to send and receive bitcoins. This is very easy and all you need is active email account. Visit BlockChain website from this link and click on Wallet link. After that you will see another page where you just have to enter your working email address and password. That’s why your account is created and now I recommend you to verify your email and mobile so that you can receive notifications about your account.
How to Send and Receive Bitcoins
Every Wallet has unique code which is used to done transactions on internet. Like if you want to receive Bitcoin from any other person you need to provide it this code you you can obtain by clicking on the Receive link located at the top of your account. The code looks like this (1LxxDWk1iBvT9jMYVYZFtHKiswUT6sCvfY) and if unique to every body. Similarly you need to have this code if you want to send bitcoin to other person.
Mine Bitcoins for Your Self
So if you want to Mine BitCoins for your self than you need a powerful Computer or GPU which can handle complex operations. For this you need to download and run the Bitcoin mining software for 24/7. If you don’t want to do this than you have another option which is called cloud bitcoin mining. In this method you invest money in any website which offer cloud mining and they will do the job for you. You sit and relax while they earn money for you on daily, Monthly and yearly basis.
Earn BitCoins
You can also earn BitCoins and other Coin by joining capatcha entry websites faucets website
First of all you need to make wallet of coins in cryptonator Signup here
Second you need to make account in faucet hub or coinpot
now is time to earn coin i will upload some banner or links you can join it and earn faucet. these website instantly pay directly to your faucet hub or coinpot wallet and after received your coin in your faucet hub account or coinpot account you can widraw your coin your Cryptonator or other wallet (Depend on your choice)





1) freebitco.in
2)freedoge.co.in
3)bitfun.co
4)moonliteco.in
5)moondoge.co.in
6)moonbit.co.in/
7)bonusbitcoin.co
8)instant-ltc.eu
9)claim2.win
10)CoinFaucet.io
Hope you like this post of ours, to read more post of similar and many more on blogging, enter your email and subscribe with us to receive updates of this blog via email or subscribe to as a reader.
today i will show you how to earn bitcoin and other coins without any investment so follow my steps
Some ways to earn bitcoins
Bitcoin is a cryptocurrency(virtual money) and a payment system invented by Satoshi Nakamoto in 2009. This is a is peer-to-peer system which means no one in involved between buyer and seller. You pay directly to other person any where in the world without need to have any bank account or transaction mode. Now you must be thinking how on earth we will verify these transactions. Well this is done by some unique network nodes(data communications equipment) which can create, send and receive information. All transactions are recorded in a public distributed ledger called the blockchain so that no one can scam you.
Create BitCoin Wallet for Free
First of all you need BitCoin Wallet in order to send and receive bitcoins. This is very easy and all you need is active email account. Visit BlockChain website from this link and click on Wallet link. After that you will see another page where you just have to enter your working email address and password. That’s why your account is created and now I recommend you to verify your email and mobile so that you can receive notifications about your account.
How to Send and Receive Bitcoins
Every Wallet has unique code which is used to done transactions on internet. Like if you want to receive Bitcoin from any other person you need to provide it this code you you can obtain by clicking on the Receive link located at the top of your account. The code looks like this (1LxxDWk1iBvT9jMYVYZFtHKiswUT6sCvfY) and if unique to every body. Similarly you need to have this code if you want to send bitcoin to other person.
Mine Bitcoins for Your Self
So if you want to Mine BitCoins for your self than you need a powerful Computer or GPU which can handle complex operations. For this you need to download and run the Bitcoin mining software for 24/7. If you don’t want to do this than you have another option which is called cloud bitcoin mining. In this method you invest money in any website which offer cloud mining and they will do the job for you. You sit and relax while they earn money for you on daily, Monthly and yearly basis.
Now is time to Earn coins without any investments so read carefully and follow my instruction step by step
Earn BitCoins
You can also earn BitCoins and other Coin by joining capatcha entry websites faucets website
First of all you need to make wallet of coins in cryptonator Signup here
Second you need to make account in faucet hub or coinpot
now is time to earn coin i will upload some banner or links you can join it and earn faucet. these website instantly pay directly to your faucet hub or coinpot wallet and after received your coin in your faucet hub account or coinpot account you can widraw your coin your Cryptonator or other wallet (Depend on your choice)





These are some Legit Website they will send you bitcoin free just click some ads you can check it on google these website are Legit and paying
now there are some faucets list they will pay directly to your faucethub or coinpot account
2)freedoge.co.in
3)bitfun.co
4)moonliteco.in
5)moondoge.co.in
6)moonbit.co.in/
7)bonusbitcoin.co
8)instant-ltc.eu
9)claim2.win
10)CoinFaucet.io
In this way you will not get huge amount of coins but still it better than nothing.
you just click this link and make account earn every second without any investment.
Hope you like this post of ours, to read more post of similar and many more on blogging, enter your email and subscribe with us to receive updates of this blog via email or subscribe to as a reader.
 |
Bitcoin digital currency could be in your wallet of the future |
Bitcoin – the virtual banking currency of the internet – has existed for several years now and many people have questions about them. Where do they come from? Are they legal? Where can you get them? Why did they split into Bitcoin and Bitcoin Cash? Here are the basics you need to know.
What Are Bitcoins?
Bitcoins are electronic currency, otherwise known as 'cryptocurrency'. Bitcoins are a form of digital public money that is created by painstaking mathematical computations and policed by millions of computer users called 'miners'.
Bitcoins are, in essence, electricity converted into long strings of code that have money value.
Why Bitcoins Are So Controversial
Various reasons have converged to make Bitcoin currency a real media sensation.
From 2011-2013, criminal traders made bitcoins famous by buying them in batches of millions of dollars so they could move money outside of the eyes of law enforcement. Subsequently, the value of bitcoins skyrocketed.
Ultimately, though, bitcoins are highly controversial because they take the power of making money away from central federal banks, and give it to the general public. Bitcoin accounts cannot be frozen or examined by tax men, and middleman banks are completely unnecessary for bitcoins to move. Law enforcement and bankers see bitcoins as 'gold nuggets in the wild wild west', beyond the control of traditional police and financial institutions.
How Bitcoins Work
Bitcoins are completely virtual coins designed to be 'self-contained' for their value, with no need for banks to move and store the money.
Once you own bitcoins, they behave like physical gold coins: they possess value and trade just as if they were nuggets of gold in your pocket. You can use your bitcoins to purchase goods and services online, or you can tuck them away and hope that their value increases over the years.
Bitcoins are traded from one personal 'wallet' to another.
A wallet is a small personal database that you store on your computer drive, on your smartphone, on your tablet, or somewhere in the cloud.
For all intents, bitcoins are forgery-resistant. It is so computationally-intensive to create a bitcoin, it isn't financially worth it for counterfeiters to manipulate the system.
Bitcoin Values and Regulations
A single bitcoin varies in value daily; you can check places like Coindesk to see today's value. There are more than two billion dollars worth of bitcoins in existence. Bitcoins will stop being created when the total number reaches 21 billion coins, which will be sometime around the year 2040. As of 2017, more than half of those bitcoins had been created.
Bitcoin currency is completely unregulated and completely decentralized. There is no national bank or national mint, and there is no depositor insurance coverage. The currency itself is self-contained and un-collateraled, meaning that there is no precious metal behind the bitcoins; the value of each bitcoin resides within each bitcoin itself.
Bitcoins are stewarded by 'miners', the massive network of people who contribute their personal computers to the Bitcoin network. Miners act as a swarm of ledger keepers and auditors for Bitcoin transactions.
Miners are paid for their accounting work by earning new bitcoins for each week they contribute to the network.
How Bitcoins Are Tracked
A Bitcoin holds a very simple data ledger file called a blockchain. Each blockchain is unique to each individual user and his/her personal bitcoin wallet.
All bitcoin transactions are logged and made available in a public ledger, helping ensure their authenticity and preventing fraud. This process helps to prevent transactions from being duplicated and people from copying bitcoins.
Note: While every Bitcoin records the digital address of every wallet it touches, the bitcoin system does NOT record the names of the individuals who own wallets.
In practical terms, this means that every bitcoin transaction is digitally confirmed but is completely anonymous at the same time.
So, although people cannot easily see your personal identity, they can see the history of your bitcoin wallet. This is a good thing, as a public history adds transparency and security, helps deter people from using bitcoins for dubious or illegal purposes.
Banking or Other Fees to Use Bitcoins
There are very small fees to use bitcoins. However, there are no ongoing banking fees with bitcoin and other cryptocurrency because there are no banks involved. Instead, you will pay small fees to three groups of bitcoin services: the servers (nodes) who support the network of miners, the online exchanges that convert your bitcoins into dollars, and the mining pools you join.
The owners of some server nodes will charge one-time transaction fees of a few cents every time you send money across their nodes, and online exchanges will similarly charge when you cash your bitcoins in for dollars or euros. Additionally, most mining pools will either charge a small one percent support fee or ask for a small donation from the people who join their pools.
In the end, while there are nominal costs to use Bitcoin, the transaction fees and mining pool donations are much cheaper than conventional banking or wire transfer fees.
Bitcoin Production Facts
Bitcoins can be 'minted' by anyone in the general public who has a strong computer. Bitcoins are made through a very interesting self-limiting system called cryptocurrency mining and the people who mine these coins are called miners. It is self-limiting because only 21 million total bitcoins will ever be allowed to exist, with approximately 11 million of those Bitcoins already mined and in current circulation.
Bitcoin mining involves commanding your home computer to work around the clock to solve 'proof-of-work' problems (computationally-intensive math problems). Each bitcoin math problem has a set of possible 64-digit solutions. Your desktop computer, if it works nonstop, might be able to solve one bitcoin problem in two to three days, likely longer.
For a single personal computer mining bitcoins, you may earn perhaps 50 cents to 75 cents USD per day, minus your electricity costs.
For a very large-scale miner who runs 36 powerful computers simultaneously, that person can earn up to $500 USD per day, after costs.
Indeed, if you are a small-scale miner with a single consumer-grade computer, you will likely spend more in electricity that you will earn mining bitcoins. Bitcoin mining is only really profitable if you run multiple computers, and join a group of miners to combine your hardware power. This very prohibitive hardware requirement is one of the biggest security measures that deters people from trying to manipulate the Bitcoin system.
Bitcoin Security
They are as secure as possessing physical precious metal. Just like holding a bag of gold coins, a person who takes reasonable precautions will be safe from having their personal cache stolen by hackers.
Your bitcoin wallet can be stored online (i.e. a cloud service) or offline (a hard drive or USB stick). The offline method is more hacker-resistant and absolutely recommended for anyone who owns more than 1 or 2 bitcoins.
More than hacker intrusion, the real loss risk with bitcoins revolves around not backing up your wallet with a failsafe copy. There is an important .dat file that is updated every time you receive or send bitcoins, so this .dat file should be copied and stored as a duplicate backup every day you do bitcoin transactions.
Security note: The collapse of the Mt.Gox bitcoin exchange service is not due to any weakness in the Bitcoin system. Rather, that organization collapsed because of mismanagement and their unwillingness to invest any money in security measures. Mt.Gox, for all intents and purposes, had a large bank with no security guards, and it paid the price.
Abuse of Bitcoins
There are currently three known ways that bitcoin currency can be abused.
1) Technical weakness – time delay in confirmation: bitcoins can be double-spent in some rare instances during the confirmation interval. Because bitcoins travel peer-to-peer, it takes several seconds for a transaction to be confirmed across the P2P swarm of computers. During these few seconds, a dishonest person who employs fast clicking can submit a second payment of the same bitcoins to a different recipient.
While the system will eventually catch the double-spending and negate the dishonest second transaction, if the second recipient transfers goods to the dishonest buyer before they receive confirmation, then that second recipient will lose both the payment and the goods.
2) Human dishonesty – pool organizers taking unfair share slices: Because bitcoin mining is best achieved through pooling (joining a group of thousands of other miners), the organizers of each pool get the privilege of choosing how to divide up any bitcoins that are discovered. Bitcoin mining pool organizers can dishonestly take more bitcoin mining shares for themselves.
3) Human mismanagement – online exchanges: With Mt. Gox being the biggest example, the people running unregulated online exchanges that trade cash for bitcoins can be dishonest or incompetent. This is the same as Fannie Mae and Freddie Mac investment banks going under because of human dishonesty and incompetence. The only difference is that conventional banking losses are partially insured for the bank users, while bitcoin exchanges have no insurance coverage for users.
Four Reasons Why Bitcoins Are Such a Big Deal
There is a lot of controversy around bitcoins. These are the top reasons why:
1) Bitcoins are not created by any central bank, nor regulated by any government. Accordingly, there are no banks logging your money movement, and government tax agencies and police cannot track your money. This is bound to change eventually, as unregulated money is a real threat to government control, taxation, and policing.
Indeed, bitcoins have become a tool for contraband trade and money laundering, precisely because of the lack of government oversight. The value of bitcoins skyrocketed in the past because wealthy criminals were purchasing bitcoins in large volumes.
2) Bitcoins completely bypass banks. Bitcoins are transferred via a peer-to-peer network between individuals, with no middleman bank to take a slice.
Bitcoin wallets cannot be seized or frozen or audited by banks and law enforcement. Bitcoin wallets cannot have spending and withdrawal limits imposed on them. For all intents: nobody but the owner of the bitcoin wallet decides how their wealth will be managed.
This is really threatening to banks, as you might guess.
3) Bitcoins are changing how we store and spend our personal wealth. Since the advent of printed (and eventually virtual) money, the world has handed over the power of currency to a central mint and various banks. These banks print our virtual money, store our virtual money, move our virtual money, and charge us for their middleman services.
If banks need more currency, they simply print more or conjure more digits in their electronic ledgers. This system is easily abused and gamed by banks because paper money is essentially paper checks with a promise to have value, with no actual physical gold behind the scenes to back those promises.
Bitcoins are designed to put the control of personal wealth back into the hands of the individual. Instead of paper or virtual bank balances that promise to have value, Bitcoins are actual packages of complex data that have value in themselves.
4) Bitcoin transactions are irreversible. Conventional payment methods, like a credit card charge, bank draft, personal checks, or wire transfer, do have the benefit of being insured and reversible by the banks involved. In the case of bitcoins, every time bitcoins change hands and change wallets, the result is final. Simultaneously, there is no insurance protection of your bitcoin wallet: If you lose your wallet's hard drive data or even your wallet password, then your wallet's contents are gone forever.
Hope you like this post of ours, to read more post of similar and many more on blogging, enter your email and subscribe with us to receive updates of this blog via email or subscribe to as a reader.
W
iFi hacking is the one most conversational topic all over the internet, we all are well aware that how tech geeky users searches for the hacking tools on internet, but really how can it be possible to hack any WiFi?
Below we have discussed Top 10 WiFi Hacking And Defending Application for Android which works on rooted and unrooted Android devices, to know all the applications just follow below!
Hope you like this post of ours, to read more post of similar and many more on blogging, enter your email and subscribe with us to receive updates of this blog via email or subscribe to as a reader.
1. WiFi WPS WPA Tester
This application is compatible with all your android device above 2.0 version, this application helps you to crack into the WiFi networks around you, but not all the routers, every router till date have some vulnerability and that helps this application to breach into the WiFi router.
2. WiFi Kill
If you are near any public WiFi network then this application will help you to block all the other users connected to the same public WiFi network, you can breach into any Wifi network around you because basically the public WiFi network has many security vulnerabilities.
3. WPS Connect
Wps connect is one of the best and popular Android application, this app helps you to crack any WiFi network around you, even you can disable connections of other users who so ever connected with the same wifi network, this application also helps you to crack passwords protected WiFi, and it takes time to crack wifi password because of the protection level.
4. ZANTI Penetration Testing Android Hacking Toolkit
This application does not require a rooted android device, this application basically created to identify the attacker but later with a mod version help attackers to attack any WiFi network and the mod version required rooted android devices.
Basically, this application used in corporate management where the IT Security Administrator demand this application to block the intruder to steal any such confidential from the firm.
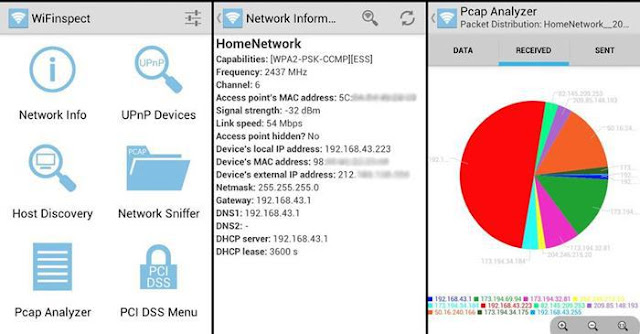
5. WiFi Inspect
This tool is basically introduced to monitor the hacking activity on the owned network, IT professionals use this software to monitor the network whether there is any intruder, also to manage the number of users on the same network, this application is a security audit tool and not for hacking.
6. Arpspoof
This application is only based on network auditing, not for hacking but some of the hardcore users steal the source code of the application to make it a hacking tool which helps them to search nearby wifi network.
The original application redirects the traffic on the local network by creating ARP replies and again able to send them to specific targets or all the hosts users on same local network paths.
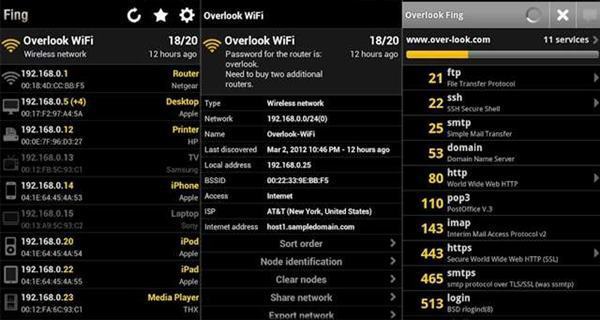
7. Fing Network Tool
This application is totally user-friendly with an amazing User interface to make the function even faster, the application helps you to analysis your WiFi network, This application works only on the android rooted device.
It helps you to find out which network or users are connected to your WiFi, the professionals use this to maintain their WiFi network, they use this application to detect the intruders and helps to resolve network issues.
8. Nmap for Android (network Mapper)
Among all the above application this one as we can call it the best! because of its popularity, it helps the users to scan the network or port to find out the intruders, previously this application developed for Unix OS but now it is available for Windows and Android. The UI of the application is much more attractive.
9. Network Discovery
This application works on non-rooted devices too, this application helps you to monitor your connected networks, and also helps to scan the nearby networks, this doesn’t help you to hack any network but yes its helps you to monitor several networks on the scan mode!
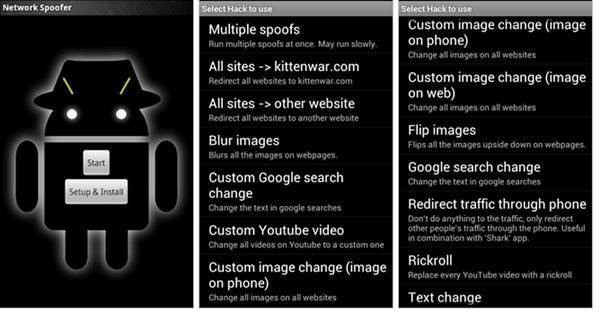
10. Network Spoofer
This application required rooted Android device because, with the help of this application, it can change website of other people’s computer connected to the same network, basically, it is not a penetration testing tool, but it helps you to analysis that how hard or easy to hack any WiFi network.
10 Free Wireless Hacking Software
T here are lots of free tools available online to get easy access to the WiFi networks intended to help the network admins and the programmers working on the WiFi systems and we at Team Techworm have picked the top 10 of those for ethical hackers, programmers and businessmen.
Internet is now a basic requirement be it office or home as it is majorly used in smartphones besides computer. Most of the times people prefer to use wireless network LAN which is much easier and cost effective.
It has been observed that the neighborhood WiFi hot-spots are visible on user’s device however one can get access to the same only by cracking password with the sole purpose of using free internet. Also in case of big firms where all the employees are connected through a wireless network admin might want to keep a check on the network traffic and hence even they need tools to crack the network.
Vulnerability in the wireless LAN is majorly due to poor configuration and poor encryption. Poor configuration includes the case of weak password mainly done purposefully by the network admin to check the network traffic. Poor encryption is dangerous as it is related to the 2 security protocols WEP (Wired Equivalent Privacy) and WPA (WiFi Protected Access) and WPA is again of 2 types WPA1 and WPA2, WPA was introduced in 2003 as WEP protocol was easy to crack. The tools used to hack the network is used either for the
purpose of sniffing the network : as is the case of network admins
cracking the password: used by programmers to rectify the trouble shooting and by the people who want to use internet free of cost. It has been seen that based on this concept there are around 10 tools
together which can be understood to hack wireless LAN.
Aircrack
Most popular wireless password cracking tool, it attacks 802.11a/b/g WEP and WPA. This tool manufacturers also provides tutorial for installation of the tool and its usage for cracking the password. Prior to using this tool it is essential to confirm that the wireless card can inject packets as this is basis of WEP attack.
Cain & Abel
This tool intercepts the network traffic and cracks the passwords forcibly using crypt-analysis attack methods. It also helps to recover the wireless network keys by analyzing routine protocols.
inSSIDer
This tool has been awarded “Best Opensource Software in Networking” and is a paid software available at a cost of $19.99. This is popular scanner for Microsoft Windows and OS X operating systems and can do a lot of tasks which can be helpful for the admins to sniff the network LAN.
WireShark
This is network protocol analyzer. So again good for the network admins to keep a check on the traffic. Basic requirement is that the user should have a good knowledge of the network protocol only then they can use this tool.
CoWPAtty
This tool is an automated dictionary attack tool for WPA-PSK. CoWPatty is simple to use however it is slow as tool uses the password dictionary for generating hack for each word contained in the dictionary by using the SSID.
Airjack
This is a Wi-Fi 802.11 packet injection tool. Mostly used to check for the “man-in-the-middle (MiTm) flaws” in the network and mitigate them.
WepAttack
This is an open source Linux tool for breaking 802.11 WEP keys. While working with this tool a WLAN card is required and basically the tool attacks working key using the dictionary words.
OmniPeek
This is again network analyzer tool working only on Windows OS. This tools captures and analyzes the network traffic. The tool can be also used for trouble shooting.
CommView for WiFi
This is for wireless monitoring and protocol analysis. Captured packets can be decoded by user-defined WEP or WPA keys. This again is mainly used to monitor the WiFi traffic by the professional programmers, protocol admins and even at homes.
CloudCracker
This is online password cracking for WPA protected WiFi networks. It is used to crack the passwords by using a dictionary of around 300 million words.
Most of these tools are free; some of them are for protocol analyzers to monitor the trouble shooting whereas others are for hacking the password for unauthorized internet access also there are tools which use the dictionary words to crack the password.
For the network admins and the professional programmers these tools should be more helpful for understanding the cracking of password and hence helping them professionally.
However, one needs to be cautious when using the tools as this might be an offense to use the tools to crack the passwords and get unauthorized access to the internet in some countries. Also such kind of tools are also used by cyber criminals and terrorists to get easy access for free usage of internet anonymously.
Hope you like this post of ours, to read more post of similar and many more on blogging, enter your email and subscribe with us to receive updates of this blog via email or subscribe to as a reader.
Here are the 15 best Android hacking apps and tools of 2016
A ndroid Hacking, which was once considered the exclusive domain of the “experts” has become very common phenomenon with the rise of technology and advancements in the mobile field. With most people relying on their smartphones and other portable devices to carry out their day to day activities, it is very important to know about the (ethical) hacking tools available on your Android smartphone.
Android smartphones can run penetration testing and security test from hacking Android apps. With the help of a few applications and basic knowledge of the true capabilities of your Android smartphone, you, too, could dig into the world of hacking.
So, here we are sharing a list of 15 Android hacking tools and apps that will turn your Android smartphone into a hacking machine.
1. Hackode
Hackode is one of the best applications for people who want to hack their android devices. The hacker’s Toolbox is an application for penetration tester, Ethical hackers, IT administrator and Cyber security professional to perform different tasks like Google Hacking, Reconnaissance, DNS Dig, Exploits, Security Rss Feed and many more.
2. AndroRAT
AndroRAT, short for Remote Administration Tool for Android, is a client/server application developed in Java Android for the client side and in Java/Swing for the Server, which is used to control a system without having physical access to the system.
3. SpoofApp
SpoofApp is definitely used for fun over functionality. It allow you to spoof (Place) calls with any caller ID number. Basically you can manipulate what number shows up on your friend’s phone when you call. Some other features includes voice changer using which we can change our voice and can even record the entire conversation. To spoof calls, you need to buy SpoofCards which are sold separately.
4. WhatsApp Sniffer
WhatsApp Sniffer is a great android hacking app, which works in tandem with the WhatsApp application. Using this app, you can hack private WhatsApp chats, pictures, audios and videos of your friends who are using your WiFi Hotspot. You can manipulate pictures, videos, account info at your pleasure. It is detected by antivirus so disable your antivirus before using this app.
5. APK Inspector
APK Inspector is a great tool that any general app user will love. It’s main purpose is to reverse engineer any android application. This means that you can get the source code of any android application and edit it in order to remove licence and credits. However, most analysts use it as a powerful GUI tool to see the workings of an Android app as well as understand the coding behind it.
6. Eviloperator
This app automatically connects two person in a phone call making them feel that they called each other. Eviloperator’s biggest merit would probably have to be that you can record and save the conversation.
7. Kill Wi-Fi
his open source ethical hacking app is one of the most popular ones in this field. Similar to the net cut app in Windows, this app is capable of cutting off anyone’s WiFi over your network. Kill Wifi is extremely useful when you have an open WiFi not protected by a strong password. You can cut off the WiFi of the intruder by just a few clicks on your device. This app is easy to use owing to its lucid and interactive interface and easy-to-use tools.
8. DroidSheep
DroidSheep is a fantastic hacking app for beginners and anyone else who wants to dabble into the hacking world. This app can be easily used by anybody who has an Android device and only the provider of the web service can protect the users. So, anyone can test the security of his account by himself and can decide whether to continue using the web service.
9. Burp Suite
Burp Suite is kind of like a proofreader or fail safe. It is an integrated platform for performing security testing of web applications. Its various tools work seamlessly together to support the entire testing process, from initial mapping and analysis of an application’s attack surface, through to finding and evaluation of potential security threats.
10. dSploit
dSploit is an Android network analysis and penetration suite to perform network security assessments on mobile phones. It is a complete toolkit so that you can perform various attacks like password sniffing, real time traffic manipulation, etc.
11. Zanti
ZAnti is one of the best android app related to hacking from android phone. It has almost all security tools related to hacking any Wi-Fi networks.
12. Shark for Root
Shark for Root is a traffic sniffer app for Android device. By using this, tools you can sniff any network and gather lots of data from any Wi-Fi network. It works fine on 3G and Wi-Fi also in Froyo tethered mode.
13. AnDOSid
AnDOSid is a tool designed only for security professionals to let them carry out DOS attack. It is used to perform a DOS attack on websites or web servers using the android device.
14. FaceNiff
FaceNiff is an Android app that allows you to sniff and intercept web session profiles over the Wi-Fi that your mobile is connected to. It also finds password of Facebook, Blogger, Twitter, Amazon, Tumblr, and more online accounts.
If you are using the same network as your victim is using and if your FaceNiff is turned on, then it will capture all Facebook ID and password which is logged in from the same Network. It comes with paid version but also there are many cracked versions on the internet.
15) Nmap for Android
Nmap is a popular network security scanner, which is also available for android devices. It is used by professionals for network exploration. It works on both non-rooted and rooted phones. However, if your device is rooted then you have access to some more features. You can download this app for your Android device. This app allows you to scan networks for finding ports and system details.
If you think we have missed out any hacking apps in the list above, you can mention them in the comments below.
Note : Based on the feedback from our readers on our previous Hacking Tools for Android article, we are giving the download link with each and every hacking tool. However, the veracity/genuineness of the download is not guaranteed by Caresofts.
Hope you like this post of ours, to read more post of similar and many more on blogging, enter your email and subscribe with us to receive updates of this blog via email or subscribe to as a reader.
W inRAR is a great utility to compress your files and protect it using a password. You can keep your data safe and save storage space by keeping it compressed in .RAR format. However, what to do if you forget the password of your WinRAR password protected file?
To crack WinRAR password protected file password, you need to recover the WinRAR file password and use it to unlock the file. There are some methods to crack WinRAR password using the command prompt, but they just work on integers and other combinations of characters.
So, all you need is a 100% working method that cracks the WinRAR password. In this detailed tutorial, we’ll be using a simple password recovery tool to recover your lost/forgotten WinRAR file passwords.
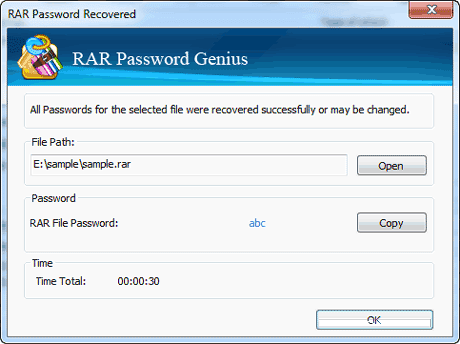
You need to use the .RAR Password Genius to crack WinRAR password and .ZIP Password Genius to crack the WinZIP Password.
In the steps described ahead, I’ll describe how to crack WinRAR password. WinRAR Password Genius is a tiny but powerful password recovery tool that is famous for high speed and guessing the complex password algorithms. It supports all the software that create the .RAR archives.
Let’s get started:
- To crack the WinRAR passwords, you need to download the WinRAR Password Genius from this link and install it on your PC. This software is the solution to all your worries and it works in three steps to complete the WinRAR password recovery.
- To start WinRAR recovery process, you need to fire-up the software and import the .RAR file into the WinRAR Password Genius. You can do this by hitting the Open button and look for the .RAR file on your computer to bring it in the Encrypted File box.
- The software uses multiple attack techniques to crack the WinRAR password. Different kinds of attacks are Brute-force, Mask, Dictionary and Smart. These are used to guess different types of passwords and you need to use these methods accordingly. Read more about these here to select the type and settings.
- Now after choosing the Type of attack from the drop-down list, select the attack type and crack WinRAR password by pressing the Start button.
- After this, the software will start its process and recover the WinRAR password for you. As the software cracks the file, a pop-up will appear showing you the password.
- Now, open the password protected .RAR file in WinRAR and you’ll see a dialog that asks for the password. Now, enter the recovered password and hit enter. This will bypass the password and now you can access your files and extract them.
To crack the WinZIP password protected files, you need to use the WinZIP Password Genius.
Did you find this how crack WinRAR password protected file tutorial helpful? Tell us in the comments below.
Hope you like this post of ours, to read more post of similar and many more on blogging, enter your email and subscribe with us to receive updates of this blog via email or subscribe to as a reader.
Your desire to master the art of Facebook hacking can harm you in a big way. Recently, a variant of Remtasu malware has been spotted in the wild that can hack your Facebook, instead of your friend’s account. Surprisingly, this malware always finds a way to remain on the system even after the victim reboots the system or tries to locate the threat in the list of active processes.
A new Facebook hacking tool has been spotted in the wild that can actually hack Facebook accounts. However, if you try to use this tool to hack someone’s Facebook account, you might end up becoming the victim of this tool.
This hacking tool is a disguised version of a Windows-based trojan whose reach has witnessed an accelerated growth over the last year. Ostensibly, the malware is now busy using social engineering tactics to target the people who are looking for ways to hack other’s Facebook accounts.
How is Remtasu Facebook hacking tool spreading?
This Win32/Remtasu.Y malware reaches your machine when you search queries like “how to hack Facebook account?” etc. As a result, you may end up downloading this Facebook hacking tool that can hack your own account.
Talking about different ways by which this trojan spreads, ESET writes, “we are no longer seeing propagation through e-mail. They are instead coming from direct download sites. Once a user downloads and executes the file, their data is compromised.”
This Facebook hacking variant of Remtasu is most common in Latin America, Thailand, Turkey and other countries.
How Remtasu hacks your Facebook account?
Once a user visits a direct download website, the malware enters in your system and disguises itself among other files. It was observed that the malware makes use of UPX compression. After the file is uncompressed, various functions are executed that include opening and capturing clipboard information, recording keystrokes and sending it to an FTP server.
Surprisingly, this malware always finds a way to remain on the system even after the victim reboots the PC or tries to locate the threat in the list of active processes. “In this case, the malware replicates itself, saving the copy in a folder that it also creates within thesystem32 folder. The new InstallDir folder remains hidden inside the system files, making it difficult for users to access,” ESET explains the process.
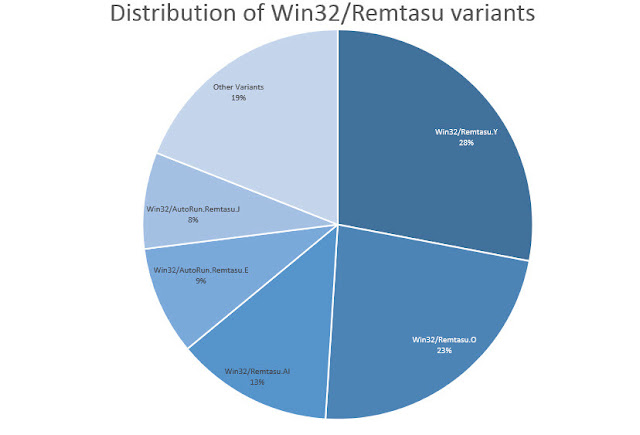
The security firm has recorded 24 different versions of the malware. Out of those, Win32/Remtasu.Y represents more than a quarter, followed by the variant Win32/Remtasu.O at 23%.
Caresofts advises the readers to stay away from Facebook hacking tools as they can harm your digital life. Also, it’s unethical.
By exploiting the SS7 flaw, a hacker can hack someone’s Facebook account just by knowing the associated phone number. This flaw allows a hacker to divert the OTP code to his/her own phone and use it to access the victim’s Facebook account. The security researchers, who have explained the hack in a video, advise the users to avoid adding their phone numbers to the public services.
Facebook hacking is also one of the most commonly searched terms on the internet. However, very often people become a victim of malware while searching for Facebook hacking tools.
As we continue to deploy new safety measures to secure our online accounts, hackers and security researchers continue to find new ways to control Facebook accounts.
Recently, we told you how an Indian security researcher spotted a bug in the Facebook website and got $15,000 bug bounty.
Today, we are going to tell you how hackers can hack any Facebook account just by knowing the associated phone number and exploiting an issue with SS7 network.
For those who don’t know, SS7 network (Signalling System Number 7) is a communication protocol that’s used worldwide by the cellphone carriers.
Using a flaw in SS7, hackers can divert the text messages and calls to their own devices. This hacking technique has been shared as a proof-of-concept video by the security researchers from Positive Technologies.
How To Facebook Account By Knowing Phone Number (Video):
This flaw affects all Facebook users who have associated a phone number with their Facebook accounts.
Affiliate marketing is a simple marketing method thorough which individuals earn money by just referring people to buy items online. This trend of marketing is flourishing day by day and most of companies prefer this type of marketing through which visitors are referred to companies outlet. The affiliates are rewarded when visitor purchase something from company or sales are done. However, different companies pay differently just as PC World pay offers 5% commission to a visitor through that a purchase is completed. The commission is different in different types of goods and it usually starts from 1% in reputable sellers and it may be 75% in few digital products. In health and cosmetic products are high in affiliates because they may offer a commission around 30%.
Affiliate marketing in now considers an amazing way to earn money online. It is famous because it is totally free to set up and any person can start this program. There is no restriction of qualification, experience and age. In affiliate marketing is a kind of marketing in which you sell someone else’s products and response you get a commission. The simple example for this online affiliate marketing is that you have a website, but do not have owned goods to sell.
How do I become an affiliate?
It is very simple to involve in this affiliate marketing, but in this affiliate marketing there are many programs and each one has its own rules and regulations. This affiliate marketing is free to join and there is not any special requirement for this. The search engine is very helpful to find out best or fantastic products. However, some companies run in-house affiliate plate form, but this specific line.
Make money tricks as an affiliate
1. It is vital that select right place for making money through affiliate program.
2. Select best affiliate program in term of commission and for this compares different affiliate programs which offer different percentage in commission.
How to start affiliate marketing
Affiliate marketing program is the best way, which is used by different companies to increase sale and customer numbers. This marketing is simple if you have a store in which you are selling something and it is difficult for you to increase sale without the help of others, but if you have 100 other people who are promoting your product and in this way your sale will be increased many-time. The store owner only pay commission when a product is sale out so it is very effective marketing in which affiliate is paid when product is sold. This system of marketing is beneficial for both companies and for the affiliate marketers.
Affiliate Marketing is an outstanding.
1. There is no need a huge amount of money to start this affiliate marketing business.
2. There is no requirement to purchase and retain goods stock with you.
3. There is no necessitating for hiring a place or building.
4. There is no such requirement of customers handling.
5. This is not your duty to send product and collect bills from customer.
Hope you like this post of ours, to read more post of similar and many more on blogging, enter your email and subscribe with us to receive updates of this blog via email or subscribe to as a reader.